With AKS you can use Nginx ingress controller as can be done with any Kubernetes cluster. However, you might want to have more integratied experience with Azure cloud services, so that other Azure serivces can easily access your applications in your AKS. Application Gateway Ingress Controller (AGIC) is a great way to implement secure ingress for AKS. Essntially, AGIC is a pod deployed in AKS, which will monitor AKS ingress resources and apply App Gatway configurations based on AKS ingress. Let's see how to enable AKS ingress using Application Gateway Ingress Controller, by creating a new App Gatway in the same virtual network of the AKS cluster.
You can use Azure portal enable AGIC for your existing AKS cluster. In networking tab you need to enable Application Gateway Ingress Controller.
Name of new app gateway defaults to ingress-appgateway and it cannot be changed. You can change the address space for app gateway if required. We will just use the default address space, which looks too large, but it is okay for testing. We can have more controll over app gatway with Azure CLI and deploying app gateway ingress controller with Azure CLI is dicussed here in documentation.
Once we save the changes in Network tab we can see a warning, which says to wait about 15 minutes until the app gatway is deployed.
Once app gatway is deployed we can see three new resources in the same resource group of the AKS cluster nodes. An app gatway, a public ip and a managed identity are cfreated.
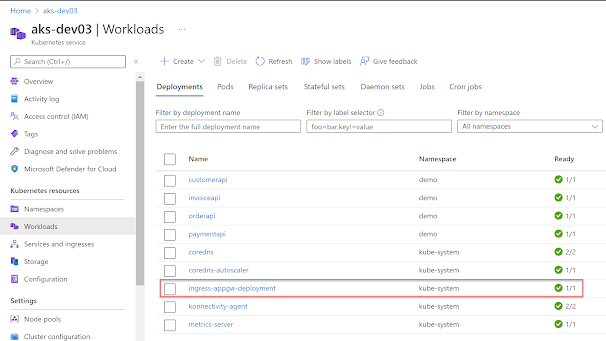
Ingress controller workload will be running in the AKS clsuter.
kubectl apply -f https://raw.githubusercontent.com/Azure/application-gateway-kubernetes-ingress/master/docs/examples/aspnetapp.yaml
The yaml above contians ingress specification to connect to the app. Below is modified yaml to deploy the app and ingress to a custom namespace named demo.
apiVersion: v1
kind: Pod
metadata:
name: aspnetapp
namespace: demo
labels:
app: aspnetapp
spec:
containers:
- image: "mcr.microsoft.com/dotnet/core/samples:aspnetapp"
name: aspnetapp-image
ports:
- containerPort: 80
protocol: TCP
---
apiVersion: v1
kind: Service
metadata:
name: aspnetapp
namespace: demo
spec:
selector:
app: aspnetapp
ports:
- protocol: TCP
port: 8091
targetPort: 80
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: aspnetapp
namespace: demomak
annotations:
kubernetes.io/ingress.class: azure/application-gateway
spec:
rules:
- http:
paths:
- path: /
backend:
service:
name: aspnetapp
port:
number: 8091
pathType: Exact
Notice in above yaml the ingress is set with annotation to use the AGIC class kubernetes.io/ingress.class: azure/application-gateway .You can apply the yaml modified above to the AKS and app will be deployed with ingress.
Using kubectl get ingress -n demo we can get the deployed ingress.
Then using the public IP show in ingress we can browse the test application which confirms the AGIC is working as expected.
We can delete the sample app with kubectl delete -f testapp.yaml -n demo once we verify the AGIC is working. How to use path based routing in AKS with AGIC can be discussed in a later post.












No comments:
Post a Comment