In last two days there was an alert in the AKS ingress app gateway, recomending to "Update VNet permission of Application Gateway users". Then starting on 20th June 2023, any newly created AKS cluster with AGIC, started to fail to manage ingess settings on app gatway for eastus region. Same behavoiur is shown in westeurope region today 21 June 2023.
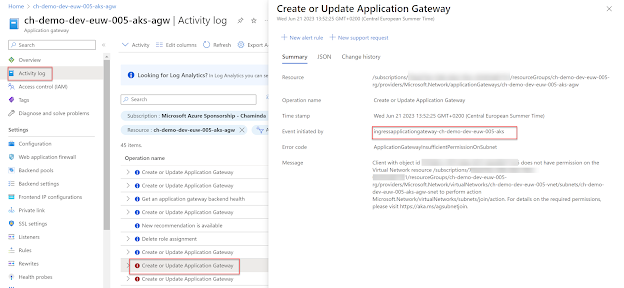
The activity logs in App Gateway has shown issues as below, making aks ingress unable to manage the app gatway settings. This was causing ingress to apps is AKS to fail.
In the advisor it provided the object id of the ingressapplicationgateway-ch-demo-dev-euw-005-aks(which is ingress identity of AKS, used to manage the app gatway for AGIC) as which is not having permision. Since the AKS cluster was created with the terraform sample here (refer blog "Create Azure CNI based AKS Cluster with Application Gateway Ingress Controller (AGIC) Using Terraform" here), as the fix Network Contributor role is added for the AKS appgateway subnet scope, for the ingressapplicationgateway-ch-demo-dev-euw-005-aks identity service pricipal.
Full code updated with above fix is made available in the terraform sample here.
Once the fix applied the AKS was able to manage the app gatway and setup ingress with app gateway settings.
Addtional links:








No comments:
Post a Comment